What is Product Vulnerability?
A product vulnerability also referred to as a security vulnerability, is defined as an exploitable glitch, weakness, or flaw found in a product or service. Furthermore, the flaw opens the door to a potential attack that could compromise a product’s integrity or functionality. Other impacts might include a breach of confidentiality.
In addition, monitoring for vulnerabilities should be an ongoing proactive process to keep up with newly added systems or discovered weaknesses.
What Is Product Vulnerability Management?
Vulnerability management is a comprehensive, multi-step process of identifying, evaluating, treating, and reporting on vulnerabilities that could impact a product’s ability to operate as intended.
The assessment process does three key things:
- Defines a vulnerability.
- Identifies and prioritizes vulnerabilities according to impact.
- Determines the appropriate actions for remediation.
4 steps in the Product Vulnerability Management Process:
Step 1: Identifying Vulnerabilities
This initial step focuses on gathering data generally through scanning. However, teams can use endpoint agents as well. This data gives organizations insight into their security landscape and potential vulnerabilities. Moreover, types of vulnerability assessment scans include network-based, host-based, wireless, application, or database.
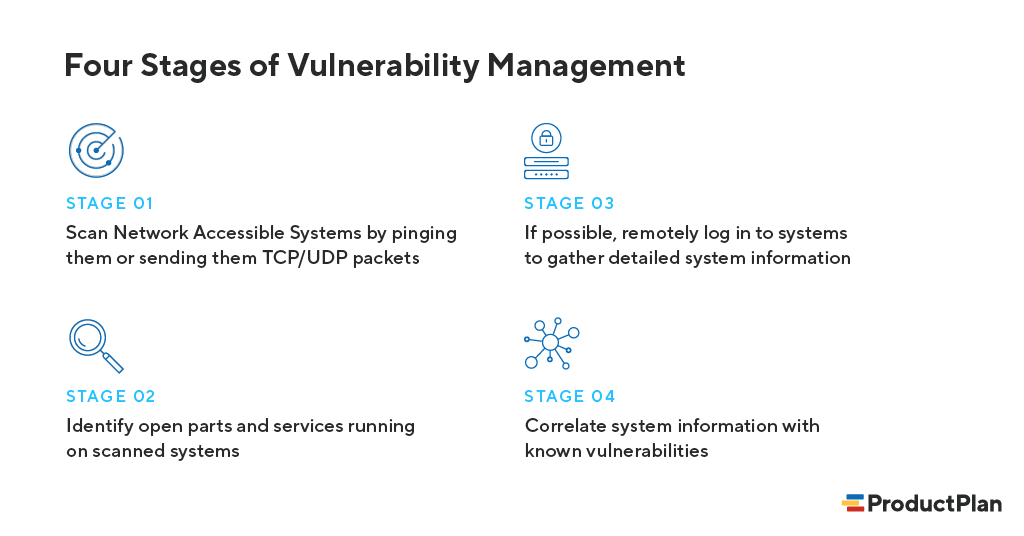
Identifying vulnerabilities includes these four stages outlined by Rapid7, a security management company (recently named a 2021 Gartner Magic Quadrant Leader for Security Information and Event Management):
Step 2: Evaluating Vulnerabilities
Secondly, this step is all about evaluating the risks any identified vulnerabilities present to be addressed appropriately. In addition to scoring vulnerabilities (e.g., Common Vulnerability Scoring System), Rapid7 suggests exploring these considerations as well:

Step 3: Treating Vulnerabilities
Thirdly, your team must take the step that requires you to treat a vulnerability like it poses a risk. In that case, the next step is to treat the exposure by taking one of three actions: remediation (i.e., fully fixing or patching), mitigation (i.e., short-term or temporary fix to reduce the impact of exploitation), or acceptance (i.e., taking no action at all).
In addition, remediation is what organizations strive to achieve, but when it’s not immediately feasible, mitigation buys organizations a little extra time to fix a vulnerability at a later time fully. Acceptance is the route organizations take when risk is low or the cost to repair the vulnerability exceeds the anticipated cost of an exploited vulnerability.
Step 4: Reporting vulnerabilities
Lastly, data gathered from the previous steps can help organizations understand their overall product vulnerability management strategy. And the security of their products or services.
Preventing Product Vulnerabilities
Preventing vulnerabilities in the first place should be part of the conversation as well.
According to Perforce, “up to 90% of software security problems are caused by coding errors, which is why secure coding practices and secure coding standards are essential.” The DevOps software company suggests these essential components for vulnerability prevention:
1. Establish design requirements that include writing, testing, inspecting, analyzing, and demonstrating code. Define and enforce secure coding principles.
2. Use coding standards like OWASP, CWE, and CERT to detect vulnerabilities and fix them.
3. Test software early and often.
Consequently, The nonprofit Open Web Application Security Project, or OWASP, improves overall software security and helps organizations prevent future cybersecurity vulnerabilities. To do this, the organization provides expertise, open-source tools, and free resources to empower and educate organizations about security. You can peruse the OWASP top 10 most common vulnerabilities here.
Kick-off, your vulnerability assessment with Synopsis’s security vulnerability assessment checklist, named a 2021 Gartner Magic Quadrant Leader for Application Security Testing.
Why Product Vulnerability Matters to Product Management
Because product vulnerabilities can pose a severe threat to a product’s integrity and an organization’s overall success, it’s essential to build security into your product roadmap.
Prioritizing cybersecurity on your roadmap communicates to primary stakeholders it is a business priority. And not just an IT issue. Product teams implement incremental improvements in every release or spread across the timeline. Even new product features require users to change passwords or use multifactor authentication to improve security.
Learn more about ProductPlan’s security.
Related terms: Technical Product Manager, IoT (Internet of Things) Product Manager, Data Product Manager, Platform Product Manager, IT Project Manager, Prioritization, Weighted Scoring, Opportunity Scoring, Implicit Requirements

